This protection technique is permitted for equipment in the Class I Division 1 and. If the content cannot be parsed into a data structure then different user agents may present it differently or be completely unable to parse it.
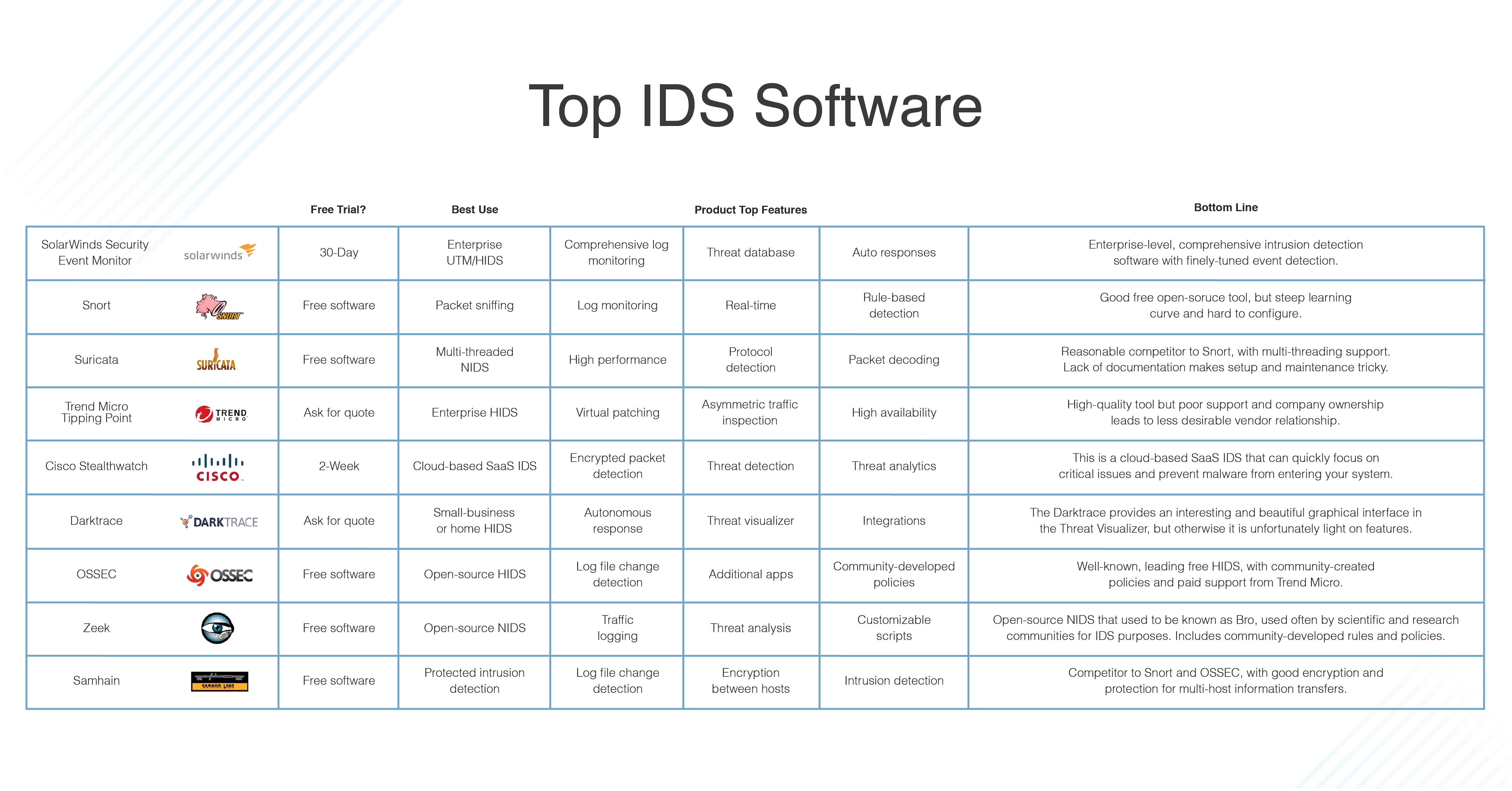
What Is An Intrusion Detection System Definition Types And Tools Dnsstuff
Which of the following IDS detection technique detects the intrusion based on the fixed behavioral characteristics of the users and components in a computer system.

. An IDS can be used to help analyze the quantity and types of attacks. However its research reveals that four types in particular are most common. It also detects on the basis of the already known malicious instruction sequence that is used by the malware.
Sneaky waits 15 seconds T2Polite. Signature recognition Anomaly detection Protocol anomaly detection All of the above. A SIEM system combines outputs from multiple sources and uses alarm.
On first login Bob is prompted to change his password. Network Node Intrusion Detection System. This method is one of the most common hacking techniques used by both novice and sophisticated hackers.
This chapter provides an overview of IDPS technologies. A Cross-site request forgery attack B Cross-site script attack C Session replay attacks D Session fixation. Paranoid Waits 5 minutes between sending each probes not detected by IDSIPS T1.
It explains the key functions that IDPS technologies perform and the detection methodologies that they use. Some user agents use repair techniques to render. A writer may use all of the following techniques to lead the reader to a flashback EXCEPT.
In this hacking technique the hacker loads the server with unnecessary traffic leading to Denial of Service DoS for authentic users. DoS and DDoS Attacks. Organizations can use this information to change their security systems or implement more effective controls.
At the most basic level Network Intrusion Detection Systems and Network Node Intrusion Detection Systems look at network traffic while Host Intrusion Detection Systems look at actions and files on the host devices. Following through on their primary objective often requires exploring the network to find their target and subsequently gaining access to it. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management system.
Host Intrusion Detection System. Fragmentation obfuscation and encryption are all evasive techniques used by attackers to dodge IDS detection. A detailed explanation C.
Answers B D and E are correct. A user named Bob Smith has been assigned a new desktop workstation to complete his day-to-day work. Command and Control.
The adversary is trying to move through your environment. Pattern Recognition Engines 3. Detection Method of IDS.
A port scanner sends a network request to connect to a specific TCP or UDP port on a computer and records the response. If you wanted to check to see if your web server was operating correctly you would check the status of port 80 on that server. Signature-based IDS detects the attacks on the basis of the specific patterns such as number of bytes or number of 1s or number of 0s in the network traffic.
Adversaries commonly attempt to mimic normal expected traffic to avoid detection. Staff may not use the restraints to lift or carry the detainee. There are various timing options included in the nmap to send successive packets.
If feasible an assistive device eg ambulatory chair gurney shall be used to help move the restrained detainee. The intent of this Success Criterion is to ensure that user agents including assistive technologies can accurately interpret and parse content. Question 2 2 out of 2 points One way to harden a system is to make sure user account names are not obvious and default accounts are disabled.
Staff may not remove restraints until the detainee is no longer a danger to himself or others. 1 environmental awareness 2 confusing automated tools 3 timing-based evasion and 4 obfuscating internal data. Any exceptions are specifically noted.
Lets begin here. Most IDSs have powerful enough pattern matching engines which will detect this trivial type of evasion technique Need to employ more complex techniques which are harder to detect String obfuscation and manipulating techniques Hex simple Unicode and UTF-8 advanced are just some examples 14 A. Network analysers are tools that allow hackers to monitor and intercept data packets sent over a network and lift the plain text passwords contained within.
Which of the following techniques is also called a one-click attack or session riding and is used by an attacker to exploit a victims active session with a trusted site to perform malicious activities. Question 1 2 out of 2 points Which of the following IDS techniques seeks to prevent intrusions before they occur. Lastline notes that an individual malware sample commonly exhibits 10 evasive behaviors.
Environmental awareness allows malware samples to detect the. An intrusion detection system is a device or software application that monitors a network or systems for malicious activity or policy violations. A clue about future events A clue about future events may not be used to lead the reader to a flashback.
Such an attack. Command and Control consists of techniques that adversaries may use to communicate with systems under their control within a victim network. Denial-of-service and access attacks are forms of attacks performed by hackers but are not directly used to compromise IDSs.
So what a port scanner does is send a packet of network data to a port to check the current status. Lateral Movement consists of techniques that adversaries use to enter and control remote systems on a network. It can be used to evade some of the rules in the firewalls or IDS.
When provisioning Bobs user account in your organizations domain you assigned an account name of BSmith with an initial password of bw2Fs3d. An intrusion detection system can also help companies identify bugs. The adversary is trying to communicate with compromised systems to control them.
The term intrusion detection and prevention systems IDPS is used throughout the rest of this chapter to refer to both IDS and IPS technologies. Staff may not use restraint equipment or devices. 1910307 f 1 Explosionproof apparatus.
T5Insane easily detectable Usage. The following are acceptable protection techniques for electric and electronic equipment in hazardous classified locations.

What Is Intrusion Detection System Ids Intrusion Prevention System Detection Web Activity
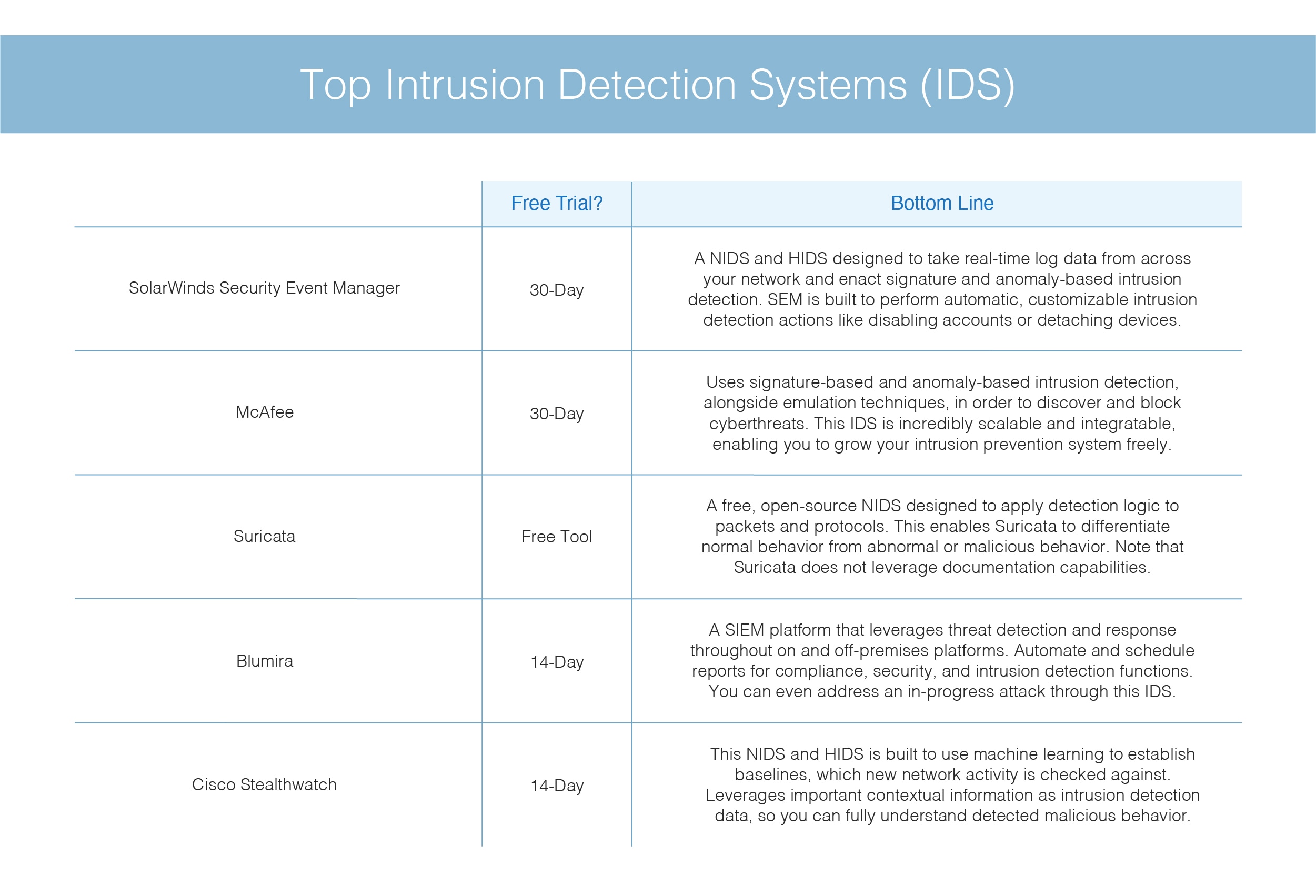
What Is An Intrusion Detection System Ids Definition And Software Solarwinds
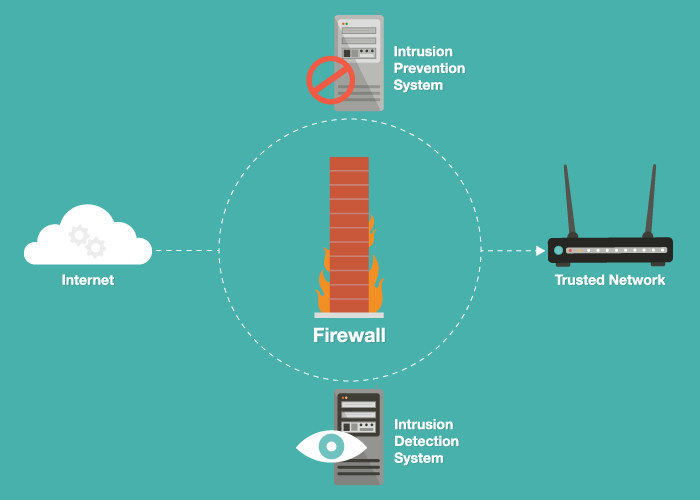
What Type Of Intrusion Detection And Prevention System Do I Need
0 Comments